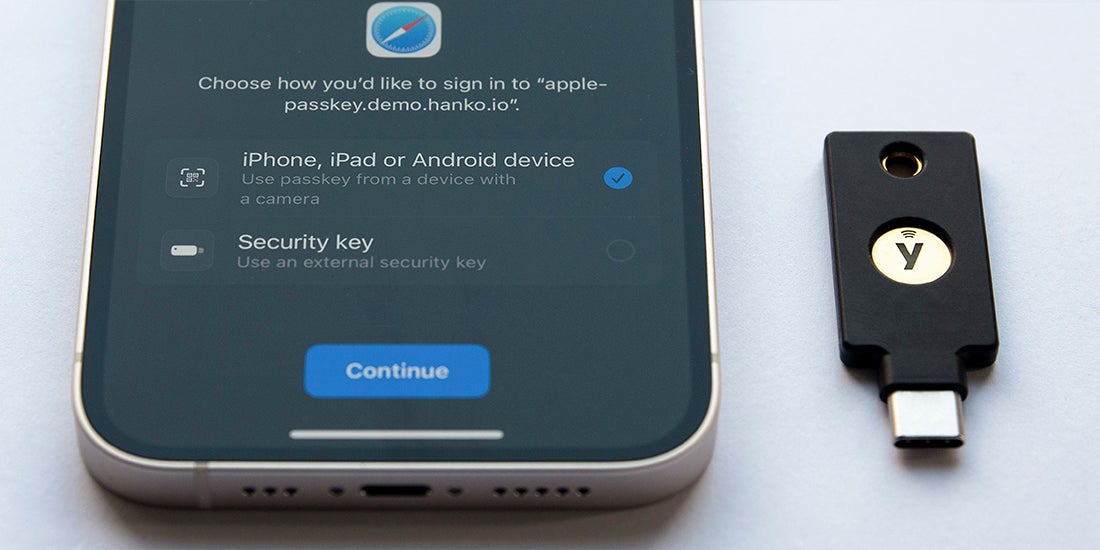
There has been a lot of information lately about the new ‘password-killing’ solution, the passkey. As we’ve discussed in previous posts on the topic, passkeys are a new industry term to make existing technology standards approachable to users. Passkeys are discoverable FIDO credentials that enable users to authenticate to websites without a password. Two types of discoverable FIDO credentials enable passwordless authentication; copyable or hardware bound.
Copyable passkeys can be synced across smartphones, tablets, and laptops/desktops and are primarily meant for consumer scenarios to help them move away from phishing-prone passwords. By contrast, hardware-bound passkeys – where the FIDO credential stays on the portable authenticator (such as a YubiKey) – are a benefit for enterprises and high assurance consumers, or just high assurance use cases.
While copyable passkeys are new to the scene, hardware-bound passkey use cases have been supported by both the YubiKey 5 Series and Security Key Series since we launched them in 2018.
Early demos of copyable passkey solutions show how the passkey is not bound to the physical authenticator, but may be copied to the user’s profile in the user’s cloud account. Ultimately, passkeys enable new user experiences and drive adoption of FIDO authentication, but copyable passkeys represent another trade-off between security and usability. Decision makers will have to choose whether they want to accept these trade-offs, including a gradient of security considerations.
(image courtesy of @vibronet via Identiverse)
Yubico’s passkey resources
We will continue to share important information so you can understand passkeys further. Our goal is to inform you so that you can make critical decisions for your business moving forward:
- Blogs:
- Webinar:
- Report:
What’s next
We are actively working on developing additional content detailing important passkey takeaways specifically for enterprises and developers who are looking for more information on what passkeys are and how to use them. We plan to publish this content in the coming weeks and months and will update this post with future content as available. Be sure to check back for the latest answers to any passkey questions you may have.